Introduction
So now we know some basic things about networking and communication and the role of IP and MAC addresses .
But how do they actually communicate?
- How do we handle the situation where data is too large to send in one piece, such as uploading a large image to a social media platform?
- What mechanisms are in place to ensure that each chunk of data sent is received correctly?
- In cases where data transmission fails or is interrupted, how do we implement a retry mechanism to ensure successful delivery?
- How can we guarantee the reliability of data transfer, especially in critical applications where data integrity is crucial?
- How do we ensure data is sent securely, especially when dealing with sensitive passwords and credit card details?
Understanding Data Communication
Before jumping into the solutions that network protocols solve, let’s first understand the problem we are trying to solve.
Understanding the problem is the first step towards finding a solution.
Picture a scenario where you just moved into a new neighbourhood and need a screwdriver to fix a broken chair. You don’t have one, so ask your neighbour if you can borrow theirs. However, there’s a challenge – you never met your neighbour before and don’t know what language they speak.
Here’s why protocols are crucial in this scenario:
- Find out what language your neighbour speaks: You must determine how your neighbour communicates and understands requests.
- Knock on the door and greet your neighbour: You establish a connection by reaching out and making your presence known.
- Let them know you are new to the neighbourhood: This information helps your neighbour understand your context.
- Let them know you need a favour: You communicate your intention, like expressing what data you want to send.
- Ask them if they have a screwdriver: You inquire about the specific information or service you need.
- Ask them if you can borrow it: You make a request, similar to how devices ask permission to send or receive data.
- Thank them for their help: You acknowledge their response, which could be a confirmation or denial of your request.
Similarly, when two computers communicate, they must follow a set of rules – network protocols – to establish a connection, convey intentions, exchange data, and acknowledge receipt. Effective communication would be challenging or impossible without these protocols, like in our neighbour scenario.
It is essential to understand that a network protocol is simply a way of formatting, sending, receiving and interpreting data. It is not a physical thing. It is just a set of rules that computers follow to communicate.
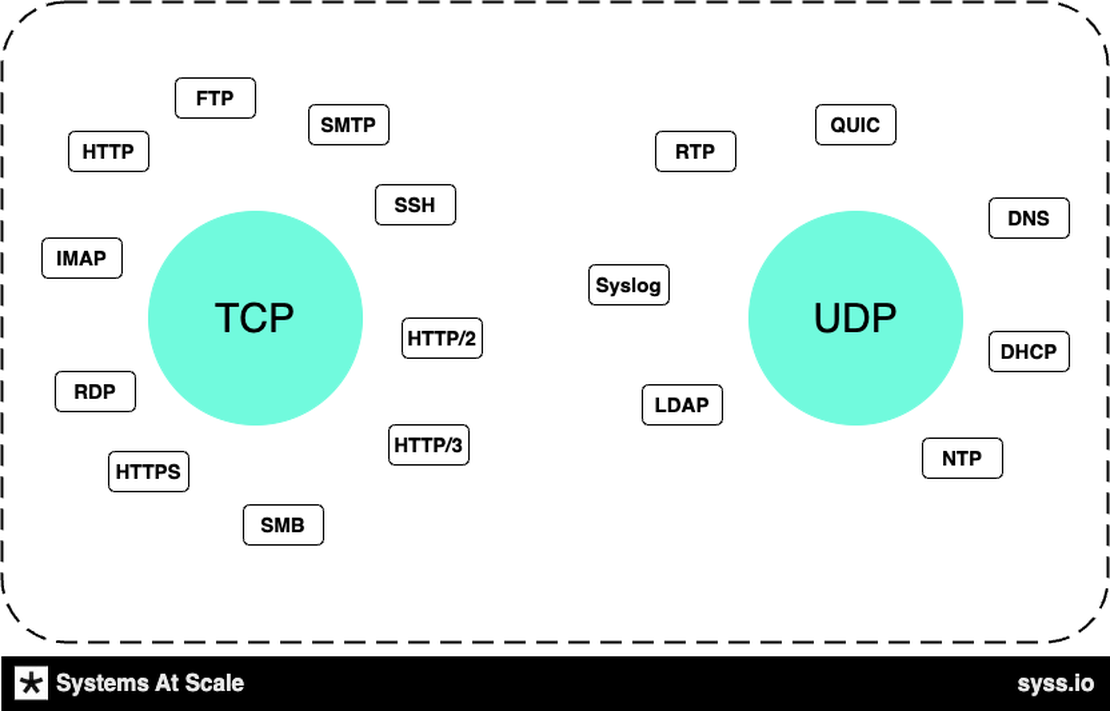
The Foundational Protocols: TCP and UDP
Two low-level foundational protocols are used in networking: TCP and UDP. They are both used for data transmission, but they differ in how they do it.
All the other protocols are built on top of these two protocols.
-
TCP (Transmission Control Protocol): TCP is the backbone of reliable, connection-oriented communication in networking. It ensures data delivery, error checking, and sequencing. TCP is like the postal service of the internet, guaranteeing that your data reaches its destination intact.
-
UDP (User Datagram Protocol): On the other hand, UDP is a connectionless, low-latency protocol that provides best-effort communication. It’s ideal for real-time applications like VoIP, online gaming, and multimedia streaming, where speed matters more than absolute reliability.
When dealing with network protocols, you may come across Network Layers . The TCP/IP model is a conceptual model that describes the network communication process at Layer 4. Since it is on top of IP and MAC addresses, layer 3 would be the IP layer, which is based on layer2 and layer1, basically the physical transmission of data, which we are not interested in at this staging. It may be referred to as the OSI model.
TCP and UPD protocols are usually supported by the operating system and are not implemented by the application developer. However, it is essential to understand their differences and when to use each.
Other protocols like HTTP, HTTPS, SMTP, POP3, IMAP, FTP, and DNS are built on top of TCP and UDP. They are used by application developers, referred to as application layer or layer 7.
Here is a quick summary of the differences between TCP and UDP:
| Feature | TCP | UDP |
|---|---|---|
| Connection-oriented | Yes | No |
| Reliable | Yes | No |
| Flow control | Yes | No |
| Error detection and correction | Yes | No |
| Latency | Higher | Lower |
| Bandwidth | Lower | Higher |
| Typical use cases | File transfer, email, web browsing | Real-time applications, streaming media |
Protocols Built on Top of TCP and UDP
With TCP and UDP as our foundational protocols, a list of protocols built on top of them but not limited to are:
-
HTTP (Hypertext Transfer Protocol): HTTP is used for fetching web pages and resources from web servers. It relies on TCP to ensure reliable data transfer.
-
HTTPS (Hypertext Transfer Protocol Secure): HTTPS, an extension of HTTP, adds encryption for secure data transfer. It’s crucial for online security and also relies on TCP.
-
SMTP (Simple Mail Transfer Protocol): SMTP is used for sending email messages, ensuring reliable delivery through TCP.
-
POP3 (Post Office Protocol Version 3) and IMAP (Internet Message Access Protocol): These email protocols rely on TCP to retrieve and synchronise emails across devices.
-
FTP (File Transfer Protocol): FTP is used for efficient file transfers, leveraging TCP for reliable data delivery.
-
DNS (Domain Name System): DNS translates domain names into IP addresses and uses TCP and UDP depending on the query type.
Practical Applications
Understanding data communication is more than just theoretical; it has practical applications. As a software engineer or developer, this knowledge is invaluable for:
- Troubleshooting network issues: When a network issue occurs, understanding how data is communicated can help you to identify the root cause of the problem.
- Designing and implementing network applications: When designing and implementing a network application, understanding data communication can help you make informed decisions about the application’s design.
- Securing network applications: Understanding data communication can help you implement security measures to protect your network applications from attack.
- Optimising network performance: Understanding data communication can help you optimise your network applications’ performance.
Conclusion
As you delve deeper into this field, you’ll encounter a wealth of protocols, technologies, and tools that facilitate seamless communication. By mastering these fundamentals, you’ll be well-equipped to thrive as a software engineer or developer, whether you’re building the next big app or ensuring the security of data transmission.